Rumored Buzz on Data Security Services
Table of Contents3 Simple Techniques For Data Security Services7 Easy Facts About Data Security Services DescribedLittle Known Questions About Data Security Services.Some Ideas on Data Security Services You Should Know
Business that takes some time to appropriately take care of as well as safeguard the safety and security of its data setting is a lot more most likely to stay clear of most attacks and also be resistant ought to the most awful occur.and innovation services supply skilled assistance and also service for your network, so you can focus on what your business does finest. Business benefits of managed solutions in combination with the cash you can conserve make it a smart solution for firms of any type of dimension. is when a business outsources particular IT works to a third-party supplier, referred to as a Managed Solution Company or.
The objective is to either offer as an IT team for a firm that has little or no interior capabilities or to sustain an experienced IT team by taking some of the day-to-day jobs off their plate. Can took care of services reduce down cost?
An in-house IT group, on the other hand, includes a lot more constant and unforeseen expenses that can rapidly drain your spending plan. Networks included a whole lot of equipment that requires to be maintained as well as occasionally repaired or changed. upkeep in addition to fixings as part of the contract, so a repair that might cost you hundreds of dollars expense is absorbed by the carrier.
The Buzz on Data Security Services
Acquiring accessibility to the most effective cybersecurity remedies and also modern technologies is a vital possession and reward to start functioning with a Managed Safety Services Service Provider. An additionally offers independent cyber-security advice; this isn't the situation for suppliers of equipment and devices. One of the primary advantages of working with a Managed Protection Solutions Provider is the broad cyber-security competence it offers, something that lots of companies don't have internal.
The accredited employees of great MSSPs are constantly mindful of advancements in the industry as well as in modern cyber threats. Organizations that put their trust fund in an are typically extra effective at securing their own organizations than when they depend on their own safety groups alone. Obviously, this does not alter the truth that both teams have to make correct plans concerning exactly how they connect with one another.
An MSSP can: Day in, day out, need to handle plenty of safety and security informs stemming from various safety devices utilized within the company. Simply put, alerts typically stop working in their function: they're either not functional or do not consist of details that can be made use of to act. This kind of sharp tiredness boosts the chance that real cyber dangers will certainly go undetected.
4 Simple Techniques For Data Security Services
Numerous cyber-security options create integration troubles when exchanging data, resulting in inefficient as well as inadequate data silos. A lot of MSSPs use the innovation of all kinds and also sizes that in-house experts have actually incorporated over time for businesses.
As well as if you require to scale back at a later time, you can. respond rapidly. The price linked with maintaining an in-house IT team is a huge one, and also that's why you often see teams get more that are understaffed, overworked as well as not able to get whatever done because of an absence of time and sources.
Educating also one added staff member for your IT division expenses countless dollars, as well as there is visit site never a guarantee that they'll even remain with the firm. An MSP soaks up the price of training, as well as you'll never ever have to worry about your IT experts leaping ship. Scaling networks takes substantial sychronisation, workforce as well as new equipment.
A Virtual CIO is a solution some MSPs offer that gives evaluation, approach and also a detailed strategy for the firm's modern technology - data security services.
All About Data Security Services
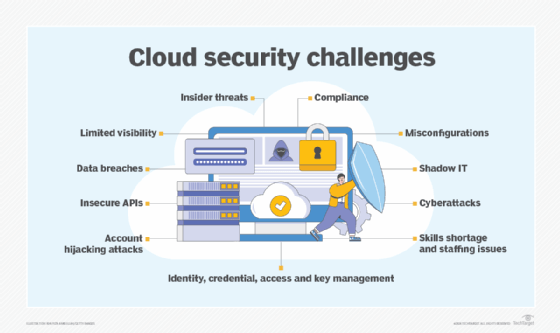
The idea of attaching individuals as well as data from anywhere at any kind of time cause the advancement of cloud computing in the 1960s. It came along with numerous safety and security hazards such as data violation, information loss, hijacking of accounts, insecure APIs, rejection of solution and insider hazards which paved method for the principle of cloud safety and security.

Disaster recovery plans can also be performed quickly when all the info is managed in one place. With the best cloud safety and security steps in position, people can safely access data and applications within the cloud regardless of where they are or what tool they make use of. Cloud computer allows organizations to grow significantly, decrease innovation costs and make use of agile methods in order to fulfill the competitors.
As the cloud system is based upon the energy, you have to pay only to the provider simply for what you make use of. Cloud computer enables several customers to access and share data while documenting at the exact same time which makes it easy for the workers who function offshore or at residence to function on the information promptly and also quickly get redirected here through any kind of web-enabled solutions.